The migration should have been a watershed moment, safely delisting inactive NFTs while transferring active listings to a new smart contract. Instead, it triggered a catastrophic theft that led to the loss of high value NFTs, spread panic across social media and dealt a hammer blow to user confidence. At time of writing, the hacker holds roughly $1.7 million worth of stolen NFTs. OpenSea has confirmed the loss of 32 NFTs. These include 3 BAYC, 17 Azuki and 2 Clonex. Users were apparently duped into signing a fraudulent contract that authorised private sales of their NFTs for 0 ETH. After widespread panic and speculation, the theft has now been attributed to a standard phishing attack but that doesn’t make it any less devastating for those involved.
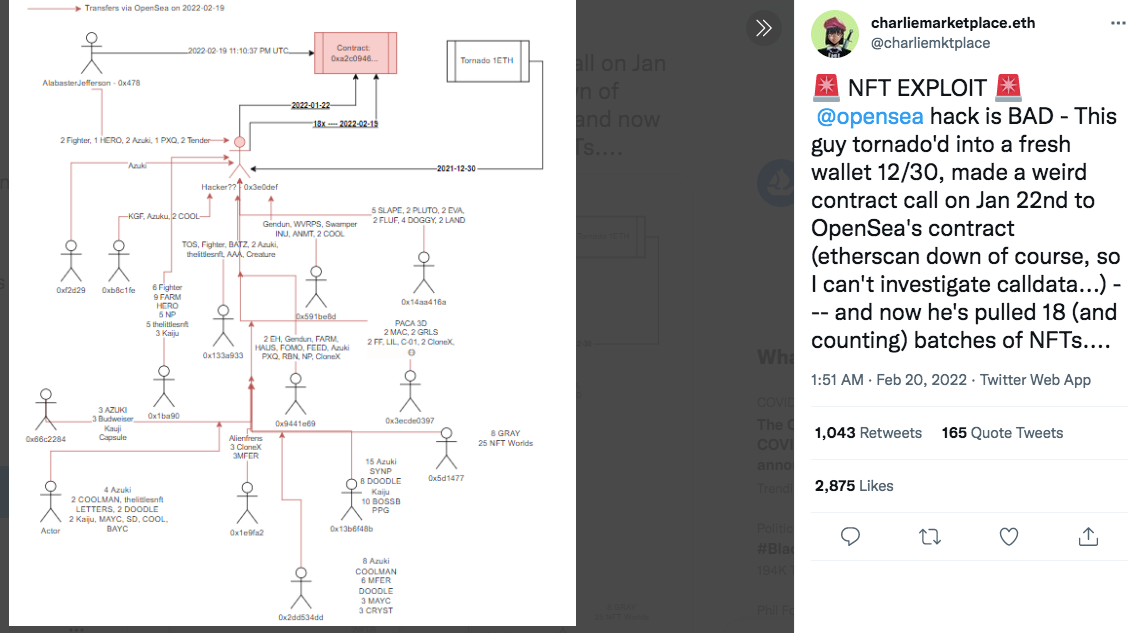
When OpenSea announced its contract migration, users were given a strict deadline of just one week before their listings expired. In theory, the migration could be completed with only a few clicks by authorising a wallet transaction. It now appears that some users were sent a fraudulent link (most likely via email, although OS says it isn’t currently aware of any fake correspondences) supposedly from OpenSea. When they clicked the migration link they actually signed a contract authorising the hacker to take their NFTs.
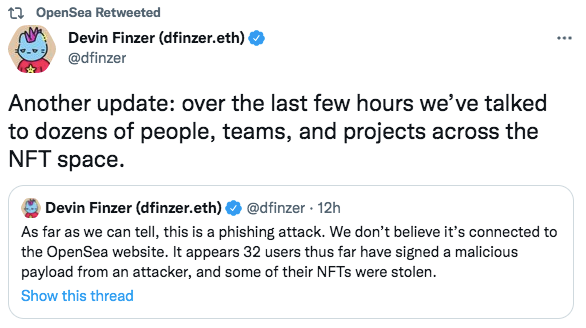
Since OpenSea imposed such a strict deadline on the migration, users were necessarily forced to act fast, making them more vulnerable. The urgency of the migration probably played a part, with people in a hurry to get the job done. In response to the news, OpenSea tweeted a warning advising users not to click on any external links.
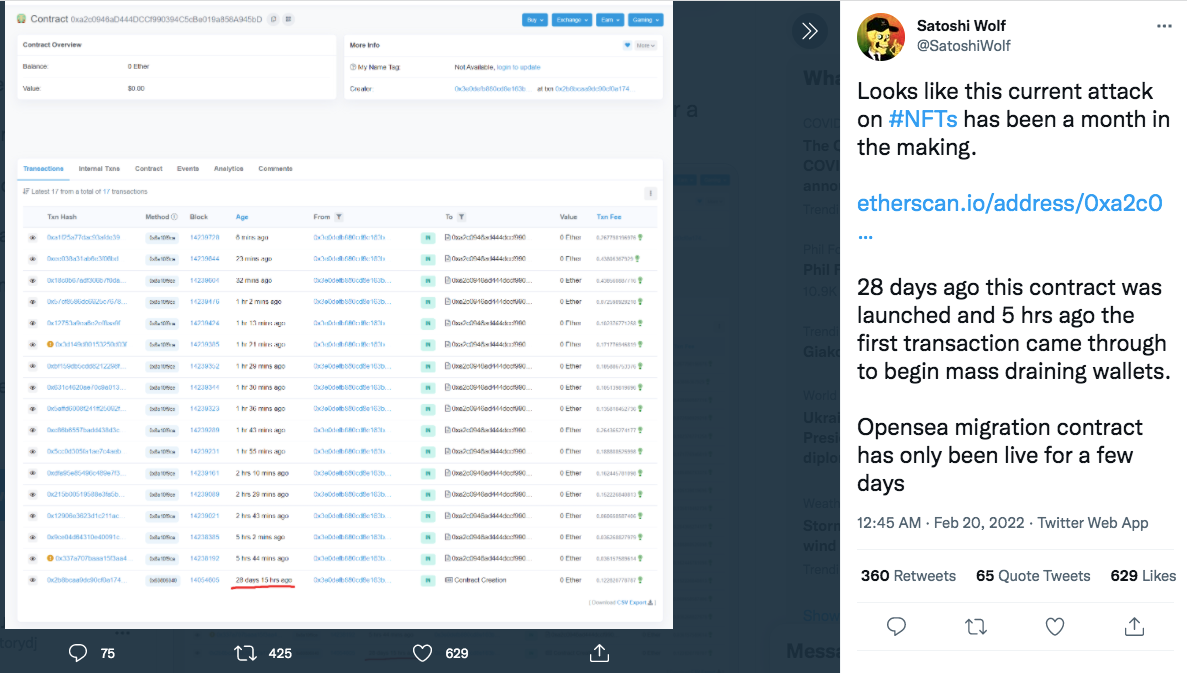
This has been a long time in the making. Transactions on Etherscan show that the fraudulent contract was uploaded 28 days ago. In the email phishing scenario, the hacker then sent fake emails and watched as signatures built up. When enough people had signed, they simply pulled the trigger and executed the theft. There’s an element of time pressure (the attack needed to be triggered before older listings expired) but the hacker was otherwise able to sit back as the fraudulent contracts were signed.
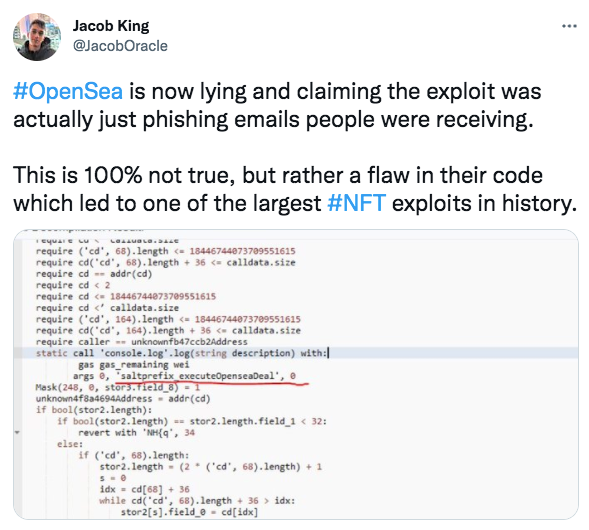
Although the attack has now been confirmed as phishing, there was initially some confusion. Conflicting and unverified reports in the early hours of Sunday spread panic across Twitter as users suggested that there might be vulnerabilities in the new contract. Some even claimed to have lost their NFTs without opening their emails or clicking any dubious links. Heaping further fuel on the fire, @JacobOracle uploaded a screenshot showing how flaws in the new contract could supposedly give hackers access to wallets. Unverified talk of an exploit in the X2Y2 contract had been buzzing around Discord, too. Now discredited, these claims made users incredibly anxious and contributed to the profound sense of confusion and unease across the community.
We urge everyone to double or even triple check the legitimacy of any transaction, signature, or link they are about to “click”. As always, do your own research, and trust information only from verified sources.
With widespread FUD, take a moment and a deep breath, before acting irrationally and possibly creating more harm than good
A recent tweet from Finzer suggests that the hack is no longer active. In a lengthy Twitter thread, he also posts links to a more technical explanation of the attack. It details how users signed half of a valid wyvern contract that was empty apart from the attacker contract and call data. The hacker then signed the other half.
Adding even more drama to the story is the brazen behaviour of the hacker. They’ve so far returned some NFTs and even sent compromised users ETH. One Twitter user reports having their Pudgey Penguins NFT returned while others talk about receiving random amounts of currency. Although it’s impossible to guess the motivations behind this kind of behaviour, the hacker certainly seems to be mocking OpenSea. As upsetting as it is for the owners, the theft of just 32 NFTs is further proof that this was pure phishing. Any flaws in the contract would (presumably) have led to a much larger attack.
What happens next is hard to predict. OpenSea has reached out, asking users to get in touch and help to resolve the issue together. Meanwhile, OpenDAO has begun seeding a compensation fund. It’s asking token holders to vote on using 170K USD to compensate victims, although they'll have to undergo a verification process that will take time. This is, however, the only glimmer of hope in what’s an otherwise miserable tale.
The saga has further dented confidence in OpenSea, with several Twitter users pointing out that even the genuine migration emails looked scammy and left ample space for hackers to infiltrate. One user even predicted - before the hack began - that the migration would lead to people losing their NFTs. Although the true nature of the hack is becoming clearer by the day, this story has rocked the NFT world and put security in sharper focus than ever before. If it can happen to a marketplace as big as OpenSea, it can happen anywhere.
This article was first written on 20/02/2022 and then updated on 22/02/2022 with clarifications as more information came to light.


