With North Korea exposed for the recent Ronin theft, there’s more attention than ever on crypto crime.
Here’s a rundown of the most prolific movers.
#9 Graham Clark
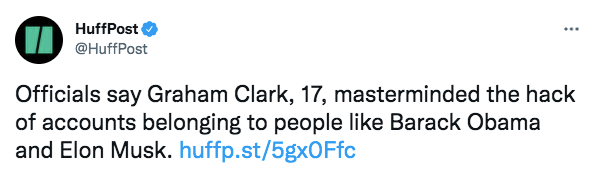
Clark might not seem deserving of a place on this list, but tell that to his victims. His methods were crude but they were effective. Clark hacked the Twitter accounts of major celebrities including Elon Musk and Barack Obama, encouraging followers to send Bitcoin which he promised would be doubled and then sent back. Surprisingly, a lot of people fell for it. The scam raised $117,000 before Clark was caught, pleaded guilty and was sentenced to 3 years in prison. He was also forbidden from using a computer without supervision, so probably doesn’t pose too much of a threat anymore.
#8 LulzSec
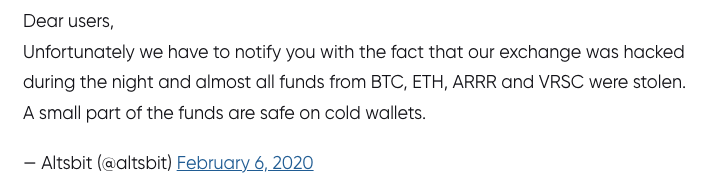
There aren't many thefts so devastating that they shut down whole exchanges. Altsbit had only been trading for a few months when it ceased operations with the following chilling message: “our exchange was hacked during the night and almost all funds from BTC, ETH, ARRR and VRSC were stolen.” Stranger still, the hacking group LulzSec (thought to be largely defunct since 2011) appeared to claim responsibility. LulzSec was behind lots of high profile hacks including the Playstation Network, the CIA and Bethesda - usually for mayhem rather than profit. Nonetheless, if the group is still out there and targeting crypto, it shouldn’t be underestimated.
#7 Morpho
The shadowy Morpho has been operating since at least 2011. Its hacks are financially motivated and they hit high profile targets including Microsoft, Facebook and Apple. Unsurprisingly, Bitcoin companies are also on their target list. They discuss their code in fluent English and appear to have flawless security protocols, but other than that hardly anything is known about them. Investigators don’t think that Morpho is state-sponsored but their methods (including zero days, multi platform malware) suggest that they’re an extremely sophisticated espionage group and one of the most powerful in the world.
#6 Wicked Panda

Otherwise known as APT41, Wicked Panda is thought to be sponsored by the Chinese government. Their charge sheet is long including attacks against telecommunications, healthcare and video game companies. The group also deploys nefarious Monero mining tools that infect compromised systems. This effectively forces the victim to mine Monero on their PC. It might not sound like much, but a single piece of rogue mining software can earn a hacker $100 million per year.
#5 CryptoCore Group
This group is confirmed as behind 5 successful exchange attacks but it's linked to up to 20 others. That makes them one of the most successful crypto hacking groups in the world, having stolen around $200 million so far. CryptoCore is also defined by its mysterious nature. Investigators (tentatively) think that it’s operating out of Eastern Europe, others suggest that it could have links to North Korea. Nobody knows, but the group’s victims are diverse - with exchanges in the US, Japan and the Middle East all hit. Hackers gather information in the first phase, researching exchange employees. Next, they launch phishing attacks; first against personal and then corporate accounts, culminating in malware insertion. Stolen passwords are subsequently used to disable two factor authentication and other security measures, giving hackers free rein.
#4 BlueNoroff
Operating out of North Korea, BlueNoroff may or may not be linked to the Lazarus Group (more on them later) but it operates uniquely. The group used to target banks and SWIFT transactions but now focuses on cryptocurrency. One of their favoured methods is to create a fake but legitimate-looking cryptocurrency company which then pushes nefarious software with inbuilt backdoors. The group is known to target crypto and DeFi startups, primarily by abusing their trust. These aren’t hit and run hacks. BlueNoroff stalks and subsequently infiltrates startups over months, embedding themselves within the infrastructure before draining funds.
#3 REvil

REvil was thought to be defunct after being dismantled by the FSB: https://www.bbc.co.uk/news/technology-59215167
REvil has a formidable reputation and might be back from the dead (its old deep website now redirects to a new page listing successful hacks). It specialises in ransomware that demands payment via Bitcoin, with the price doubling if the demand isn’t met promptly. Back in July, they demanded $70 million in Bitcoin for a universal decryption key. JBS Foods (who paid $11 million) and Kaseya were some of the highest profile hits. By then, REvil’s ransomware had infected one million systems. Some funds were confiscated by the FBI and Russia claims to have dismantled the group, but if REvil is back in business everyone should be on their guard.
#2 Lazarus Group
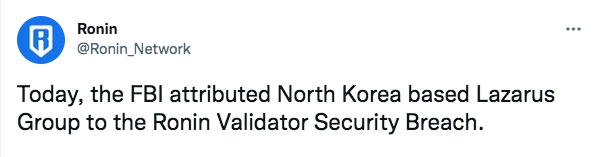
Recently outed as being behind the $600 million Ronin theft, responsible for the 2017 WannaCry ransomware and the masterminds behind countless exchange heists, North Korea’s Lazarus Group is prolific. The DPRK trains its hackers at Mirim College and centralises them at the country’s cyber unit: the dreaded Bureau 121. From there, they steal money for the country’s sanction hit coffers. As well as Ronin, Lazarus also stole $7 million from South Korean Exchange Bithumb, 4,5000 bitcoins from Nicehash and 17% of all crypto on the Youbit exchange. The state-sponsored group is sanctioned by the US but knowing the identity of some of the attackers hasn’t blunted their threat.
#1 Alpha and Beta

Imagine a pair of hacking groups so powerful that they’re responsible for a staggering 60% of all exchange hacks - around $1 billion. Virtually nothing is known about these two groups other than that Alpha is the bigger and takes more care hiding its funds (sometimes via up to 15,000 transactions). It’s thought to be a vast, centrally controlled group with the scope for huge and coordinated attacks. Beta is more disorganised and purely focused on money. It also holds stolen funds for longer (sometimes up to 18 months until the heat dies down) whereas Alpha cashes out much faster. It took an extensive Chainlink investigation to uncover even these details, and that’s where the trail ends.
Read more:
Hackers Wanted: Dead or Hired
REVEALED: Is This The Man Behind Ethereum’s Biggest EVER Hack?
Bitcoin Washers Caught in the Act


