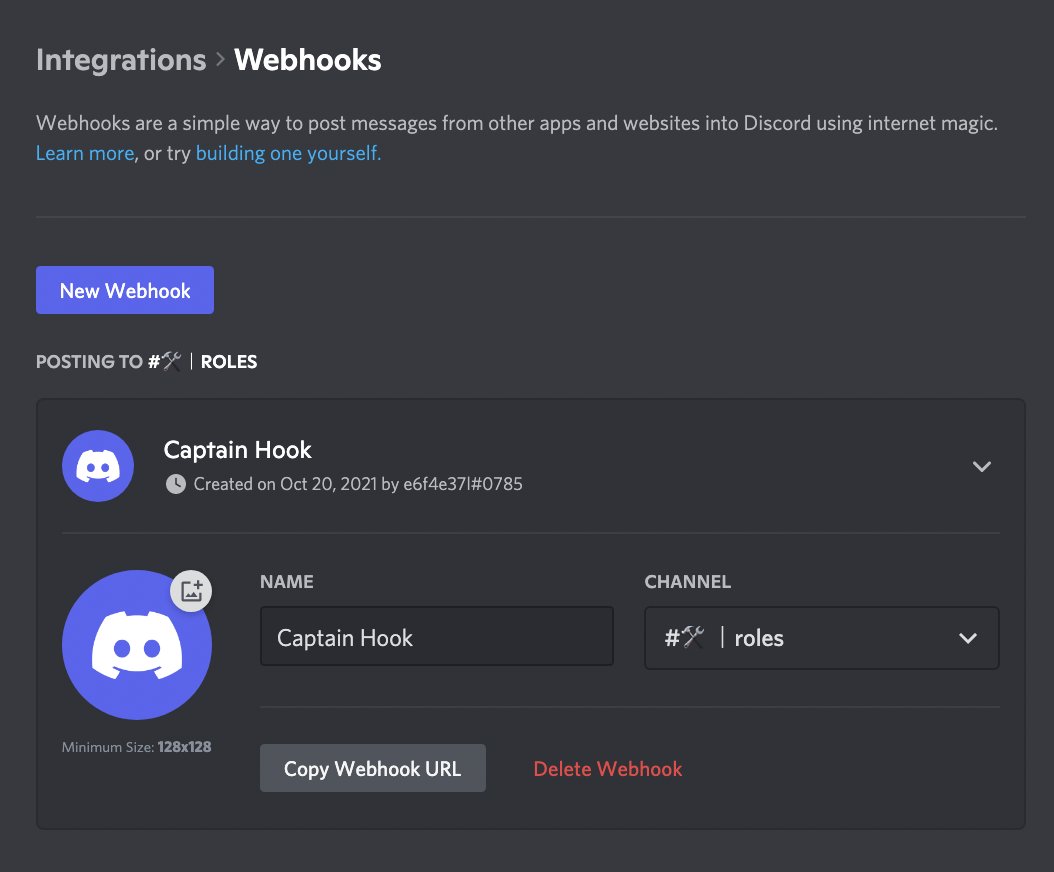
Early last week, the CreatureToadz Discord server was exploited using a phishing webhook to gain access to server controls. The user compromised one of the moderator’s permissions and upgraded its role, which allowed it to post a fake announcement of a new stealth mint through a fake URL that directed funds into the scammer’s wallet. A webhook is an application that provides other applications with real-time data. On Discord, webhooks are used to continuously check specified data points about users, but are also frequently used by scammers to send automated messages when something happens, such as a user joining a server.
It took around 45 minutes for the moderators to regain control of the server, but the exploit had already been executed, draining 88 ETH from unsuspecting users. Chain analysts rushed to track wallets and transactions. At the same time, the CreatureToadz team held a stream on Twitter Spaces to address the situation. It didn’t take long to identify the 17-year old scammer’s wallet, which was associated with a ROBLOX account, which eventually led to aTwitter profile and a Binance account owned by the scammer’s mother. Incidentally, the scammer was in the Twitter Spaces keeping an eye out on the progress of the investigation.
can't help but think the creature toadz scammer might've been listening into this spaces tonight. and because we made progress on an investigation together, they realized there was too much risk to not returning the 88 eth. that's what community is about.
— Andrew Wang (@andrwwang) October 20, 2021
Following the discovery, the CryptoToadz team fired a warning shot to the scammer to return the funds, asking him to do the right thing. Once he realized that he would likely be publicly doxxed, the scammer contacted the team indicating his willingness to return the funds to the project creator’s wallet, which he quickly did.
The lead investigator was OKHotshot.eth, who collaborated with vgf.eth. At some point, they reached out to the scammer to learn his point of view. The scammer told them that he had run the scam as a joke and out of boredom, and, conveniently, had planned to return the stolen funds all along.
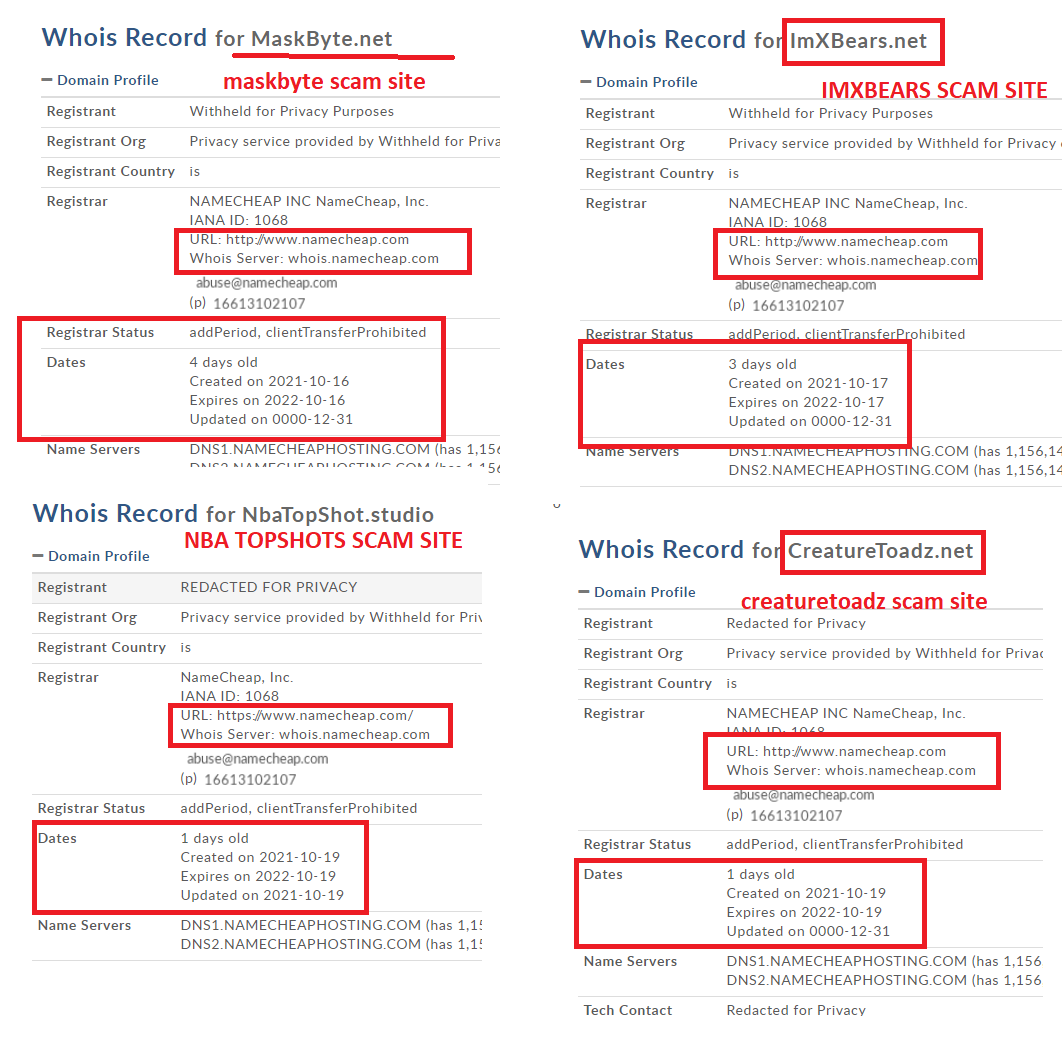
Soon after, it was noticed that Creature Toadz wasn’t the only project to have been under this mode of attack that day—the NBA TopShots Discord was targeted in the exact same fashion earlier.
News quickly spread and other communities were notified about similar hacks, with further investigations revealing a pattern of scams:
- On October 17, MaskByte was hacked with webhooks, which some claimed was a rug (later discredited by the creators)
- On October 18, IMX Bears was hacked with webhooks ( with a loss of approximately 80 ETH that hasn't yet been returned)
Since then, projects across the NFT space have been reviewing and managing bot permissions. To upgrade security measures you may want to disable or remove webhooks unless absolutely necessary.
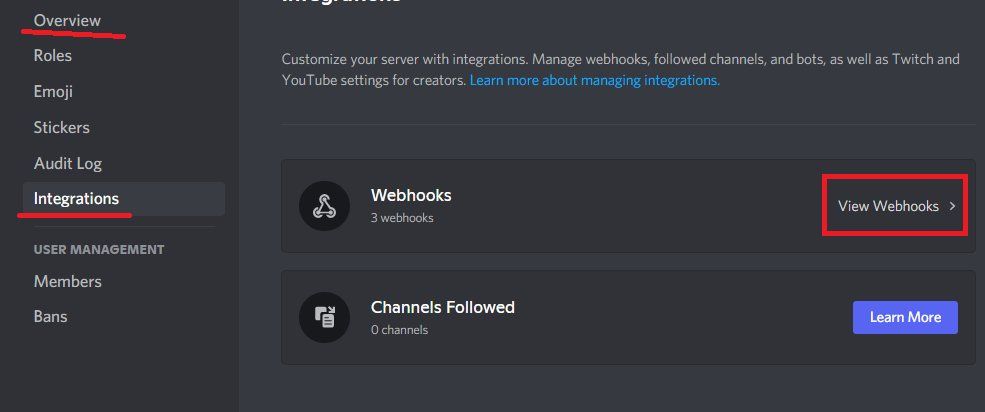
- Go to server Settings, Overview
- Click Integrations, View Webhooks
- Disable available webhooks
The hack typically works on servers with lower security by targeting bots with higher-level access. The scam cannot harm users unless they approve transactions on the link provided in the scam message.


